For the latest reported phishing emails, please visit www.chapman.edu/security
»Trending Email Scams
Chapman University’s Information Systems and Technology department monitors the trending scams in the Information Security World. We use intelligence feeds shared with peer institutions in Higher Ed as well as emails sent to abuse@chapman.edu.
Job Offer (Check Deposit) Scams
How Does a Job Offer (Check Deposit Scam) Work?
The Check Deposit Scam starts with a Job offer and ends with something similar to:
" I transfer to your account $3000, you transfer $2000 to another account."
99% of the time, the scam starts with a decent job offer. It is not "too good to be true" so it does not raise any suspicion. It looks like a good opportunity.
The perpetrators prefer to compromise a Staff, Faculty or Student account and use the compromised email account to send hundreds or thousands of emails. Sometimes, they recommend someone else by providing an email address not related to Chapman University.
They could also recommend using your personal email address - this way, the Chapman University security controls are evaded.
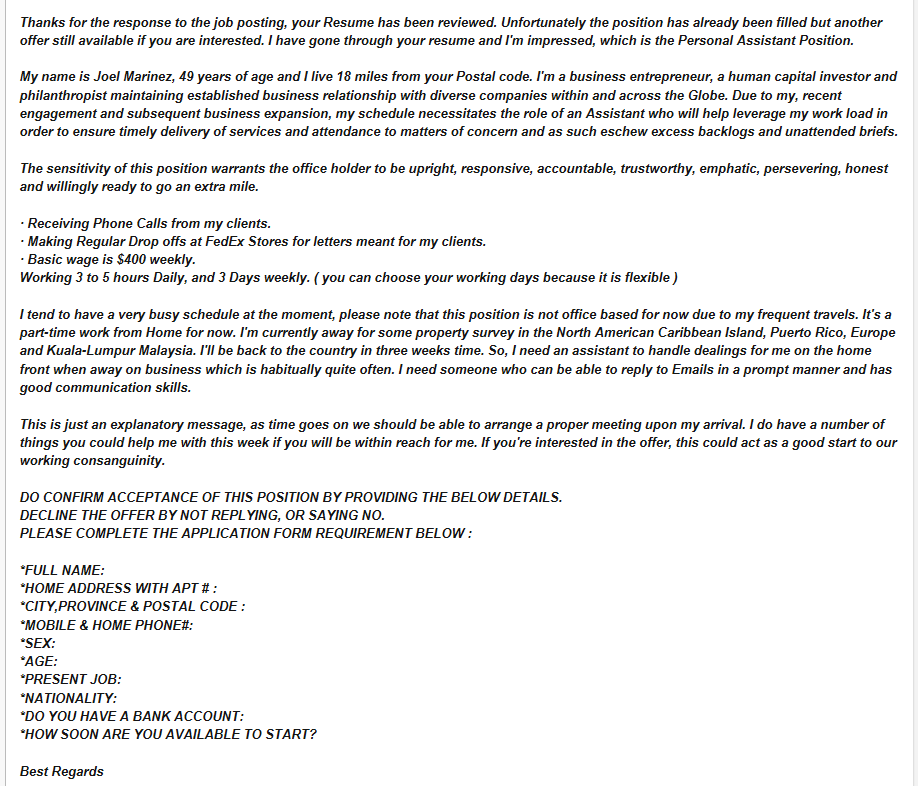
In the check deposit scam, the scammer tries to trick you into depositing a check that is not covered in your bank account. To make it look like a legitimate business, they will offer you a job (scholarships and grants have also been spotted in the wild). If it it's a job offer, they will ask for personal information from you. Some scams include a survey at the end so it feels more like a job offering.
The scammer issues you a check for $3000 although your payment would be $1000. Then, they ask you to transfer the remaining $2000 from your account to a third-party account that is usually offshore.
There are different variants of the scam, some pretending to be scholarships, grants or some opportunity for you to receive money.
Resources:
https://www.doj.nh.gov/consumer/dont-cash-that-check/check-overpayment.htm
https://www.bbb.org/article/scams/14042-bbb-tip-fake-check-scams
Why Does It Work?
To you, this is one transaction and it seems as if you're dealing with one person. However, to the bank, this is two different transactions. The bank is dealing with two different people - there is you who deposits the check and the receiver of your transfer.
The issuer of the check is in a different time zone so the check takes a while to clear. By the time you receive the notification that the scammer's check to you was not covered, your transfer for the $2000 was still initiated from your account. The bank sees you as liable even if you do not have sufficient funds.
Example of a Job Offer (Check Deposit) Scam
What To Do If You Received a Check Deposit Scam Email
Do not reply to the email message.
Do not provide any personal information, this information could be used for other scams such as the tax email scam.
Forward the message to abuse@chapman.edu
To learn more about what to do if you received a phishing email, please visit www.chapman.edu/phishing
If you are a victim of a Check Deposit scam, please review the Chapman Board Disclaimer.
You can also file an IC3 Report: https://www.ic3.gov/Home/ComplaintChoice
If unsure if a job offer is legitimate, check the job red flag resources available on Handshake (valid student log in is required)
Combination: Pretext & Phone Based Scams
What Are Combination Email and Phone Based Scams?
Attackers use a variety of methods to trick victims into giving them money.
They may combine a variety of social engineering techniques to accomplish their goals. Chapman has seen a rise in these types of attacks that move from a simple scam email (pretexting) to phone-based conversation (using social engineering) to compromise your computer.
Example of Pretext Email Scam
Sent: Tuesday, July 13, 2021 12:47 PM
To: Doe, John <jdoeeee@chapman.edu>
Subject: John Doe Order# GZ258963147
Order Confirmed Geek Squad Team
Item Qty Price Total
SONY XBR-70A8H – 70” Smart OLED 4K UHD TV 1 $1,499.00 $1,499.00
Arrives by Friday June, 2021
_________________________________________________________
If you have any questions, please call us +1-800-123-4567
Please do not reply to this email as the mailbox is unmonitored.
Thanks, Your BestBuy Geek Squad Team +1-800-123-4567
How Do Pretexting Emails Work?
The way the email is constructed aims at creating panic from the illusion that a purchase has been made using the victim’s account. Note that the email does not contain any links to the Geek Squad official website.
In this email, the user is only provided a phone number to call and is instructed
not to reply to the email. A panicked user would then call the phone number where
the scammers would be waiting to start the next phase of their ruse. Common motifs
involve robocall from the IRS, Social Security Administration or emails about services
and purchases that were never initiated by the person who is being targeted.
In some cases, they simply instruct the users to download a remote access tool hoping
that the user would allow them access to their computer. Once the scammers gain access
to your computer, they can lock it using a Windows native program to encrypt it, then
they ask for money to provide you with the password to decrypt it.
It is not uncommon to sell some fake service for a “special price”. Once the money has been paid they can either steal the credit card information, point to a free-to-use service or simply vanish.
What To Do If You Receive a Scam Email or a Call?
If you receive a random robo call or receive an email similar to the one above, ignore
it. Don’t let the bad guys gain access to your computer or directly connect to it.
Many users now have remote access to the Chapman network via VPN where the bad guys
could compromise sensitive data.
Always check phone numbers and links from emails. If there is anything suspicious,
go directly to the website in question, avoid links in emails, and check phone numbers
directly from websites.
Don’t give into pressure from the scammers. They are good at making their victims
feel nervous and coercing them into doing things they wouldn’t typically do.
When pretending to be IRS or Social Security Administration, it is not uncommon for the scammers to use strong language and swear words in order to put the victim in a panic state. “Pay up or go to jail”, “Are you stupid?!” If it seems suspicious, take a minute to think about the situation without giving them what they want.
Unemployment Insurance Claims Scam
What is "Unemployment Insurance Claim Scam"?
A large-scale scam involving phony unemployment benefits claims has been making headlines. Criminals are filing claims for benefits, using the names and personal information of people who have not lost their jobs.
Most people learn they’re affected when they get a notice from their state unemployment benefits office or their employer about their supposed application for benefits. By then, however, the benefits usually have been paid to an account the criminals control.
How does the Unemployment Insurance Claim Scam work?
The Scammers will:
- Obtain the victim’s personal information such as: name, date of birth, social security number, address, and most likely employment history. Most likely, the information is obtained from massive data breaches.
- Open a bank account in the victim’s name with an online bank such as GoBank or Green
Dot - to receive the unemployment benefit payments. Since this is not a credit account,
a credit check will not be triggered and will work even if the victim’s credit file
is frozen.
- File a claim with the state’s unemployment office, impersonating the victim, and claim that the person was laid off. If the claim is approved, the scammer receives the payments, and gets the money out of the system with the help of a money mule.
The US Secret Service had information suggesting that the scheme was coming from a well-organized Nigerian fraud-ring.
What To Do If You Are The Victim of an Unemployment Insurance Claim Scam?
The FTC advises people who were victims of the Unemployment Benefits Scams to:
- Report the fraud to your employer. Keep a record of who you spoke with and when.
- Report the fraud to your state unemployment benefits agency. You can find state agencies here.
- -If possible, report the fraud online. An online report will save you time and be
easier for the agency to process.
-Keep any confirmation or case number you get. If you speak with anyone, keep a record of who you spoke with and when. - Visit IdentityTheft.gov to report the fraud to the FTC and get help with the next important recovery steps. These include placing a free, one-year fraud alert on your credit, getting your free credit reports, and closing any fraudulent accounts opened in your name. IdentityTheft.gov also will help you add a free extended fraud alert or credit freeze to your credit report. These make it more difficult for an identity thief to open new accounts in your name.
- Review your credit reports often. For the next year, you can check your reports every week for free through AnnualCreditReport.com.
This can help you spot any new fraud quickly.
One other thing: The unemployment payments usually are deposited to accounts the imposters control. But sometimes payments get sent to the real person’s account, instead. If this happens to you, the imposters may call, text, or email to try to get you to send some or all of the money to them. They may pretend to be your state unemployment agency and say the money was sent by mistake. This a money mule scam and participating in one could cause you more difficulties.
If you get benefits you never applied for, report it to your state unemployment agency and ask for instructions. Don’t respond to any calls, emails, or text messages telling you to wire money, send cash, or put money on gift cards. Your state agency will never tell you to repay money that way. Anyone who tells you to do those things is a scammer. Every time.
For more information, please visit the FBI gov and FTC gov websites.
Covid-19 Scam Emails
How do Covid-19 Email Scams Work?
Scammers make use of the current COVID-19 crisis to trick people into getting their
computers infected with malware and giving away their bank or personal information.
Covid-19 themed scams might allude to national headlines to lend a veneer of credibility
and make them more appealing.
These scam emails will have an enticing subject and message such as (but not limited to):
- Covid-19 Vaccine
- Testing for free
- Stimulus checks
- Infection map
- Covid-19 Antivirus
- Someone you know is infected with the Novel Coronavirus (Covid-19)
The malicious emails work in the same way as regular phish emails do:
- Masquerade as a legitimate email
- Pressure the recipient of the email to click on a link or download an attachment
- Steal information entered into a fake login page or infect a computer and exfiltrate information
What To Do If You Receive a Covid-19 Email Scam?
DO NOT click on any of the links or enter any information.
Go to the source! If the email pretends to be from the Center for Disease Control, go directly to CDC.gov
Do not reply to the email message.
Forward the message to abuse@chapman.edu
Sextortion Email Scam
How Do Sextortion Emails Work?
A sextortion scammer sends out messages with spoofed email addresses using passwords obtained from "Credential Dumps". A credential dump is a list of email addresses, passwords and other personal information published online without permission. Scammers exploit credential dumps by including your password in their message to grab your attention.
A sextortion scammer claims to have compromised the target's computer to gain their passwords and personal information, but most importantly has recordings of the recipient performing intimate acts using the computer's webcam.
The scammer then asks for a "fair price" in bitcoin so they do not release the screenshot or recording to the target's social media accounts and contact lists.
Example Sextortion Email
Hello XXXXXX@
My nickname in darknet is barnett26.
I'll begin by saying that I hacked this mailbox (please look on 'from' in your header) more than six months ago,
through it I infected your operating system with a virus (trojan) created by me and have been monitoring you for a long time.
Even if you changed the password after that - it does not matter, my virus intercepted all the caching data on your computer
and automatically saved access for me.
I have access to all your accounts, social networks, email, browsing history.
Accordingly, I have the data of all your contacts, files from your computer, photos and videos.
I was most struck by the intimate content sites that you occasionally visit.
You have a very wild imagination, I tell you!
During your pastime and entertainment there, I took screenshot through the camera of your device, synchronizing with what you are watching.
Oh my god! You are so funny and excited!
I think that you do not want all your contacts to get these files, right?
If you are of the same opinion, then I think that $500 is quite a fair price to destroy the dirt I created.
Send the above amount on my bitcoin wallet: 1MN7A7QqQaAVoxV4zdjdrnEHXmjhzcQ4Bq
As soon as the above amount is received, I guarantee that the data will be deleted, I do not need it.
Otherwise, these files and history of visiting sites will get all your contacts from your device.
Also, I'll send to everyone your contact access to your email and access logs, I have carefully saved it!
Since reading this letter you have 48 hours!
After your reading this message, I'll receive an automatic notification that you have seen the letter.
I hope I taught you a good lesson.
Do not be so nonchalant, please visit only to proven resources, and don't enter your passwords anywhere!
Good luck!
What To Do If You Received A Sextortion Email Scam
Change your password immediately by going to password.chapman.edu.
Forward the email received to abuse@chapman.edu.
The Gift Card Scam - Are You There?
How Do Gift Card Scams Work?
Gift card scammers send out messages using spoofed email addresses impersonating your boss or the president of your university. The email usually has an urgent tone, asking you to buy multiple gift cards and sending them the codes on the back. Email scammers ask for gift cards because they are immediate and untraceable.
The gift card scam is also known as the 'Are You There' scam because the scammer initially sends an 'are you there' or 'are you available' message and awaits for a response before they ask you to buy gift cards.
Example Are You There? Email
Date: March 5, 2019 at 8:13:39 AM PST
To: xxxxx@chapman.edu
Subject: Urgent
Are you still available i need your help, I want you to help me out on something important ?
I am in a meeting right now and call is not allow here, are you free to help me
Daniele C. Struppa
What To Do If You Received A Gift Card Scam Email
Check with the email sender through a different mode of communication if they sent the message (In-person, Chapman Email, Desk Phone Number).
Do not reply to the email and forward the message to abuse@chapman.edu.
Phishing for Credentials
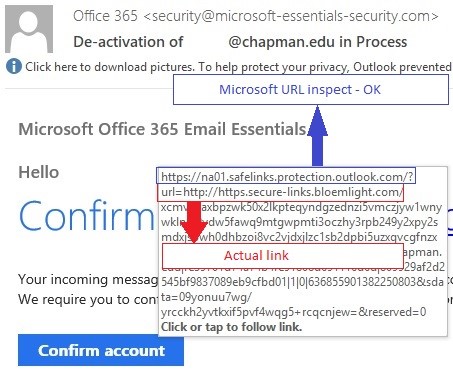
How Do Phishing Emails Work?
Phishing is the most common type of email scam with nearly 1.5 million phishing websites created each month according to Webroot Threat Report.
Phishing is when cybercriminals pretend to be a trustworthy entity and send emails to further entice their victims to
- Provide usernames or passwords
- Open viruses infected files
- Open attachments that input malware on the device allowing passwords to be stolen
More information on phishing can be viewed at www.chapman.edu/phishing
Example of a Phishing Email
What To Do If You Received A Phishing Email
- Check www.chapman.edu/security for recent phishing emails to see if the email you received is posted
- Even if you do not see it on the website still report it! It might be a new attack
- Report all suspicious emails to abuse@chapman.edu
- Always double check the sender/url before entering any usernames and passwords. If in any doubt DO NOT enter your username or password, instead ask abuse@chapman.edu to confirm legitimacy of email
For more information on what to do if you received a phishing email view www.chapman.edu/phishing
Seasonal Scams
How Do Seasonal Scams Work?
Seasonal scams, also known as holiday scams, are malicious emails that resurface every year during annual holidays and events.
Similar to phishing emails, seasonal scams are after your username and password, personal information and money. Seasonal scammers will send out emails during tax season and holidays to give their scams more credibility.
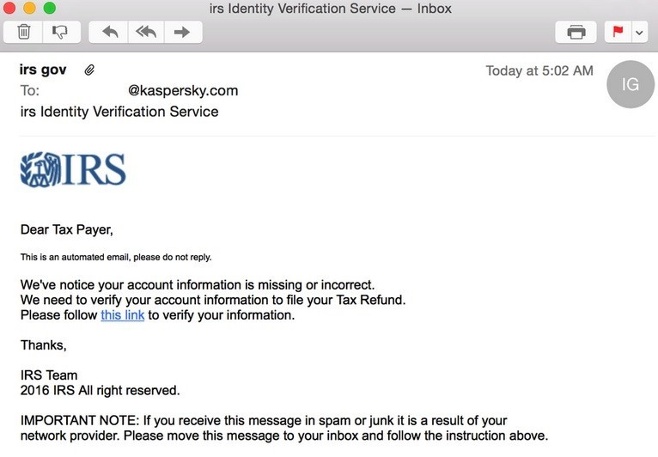
Tax Return Scam
- The scammer impersonates an IRS official and accuses the target of owing the IRS money which must be paid immediately through a wire transfer or prepaid debit card.
- The recipient is often threatened with jail time in order to scare people into giving the scammer personal information, credit or debit card numbers or money.
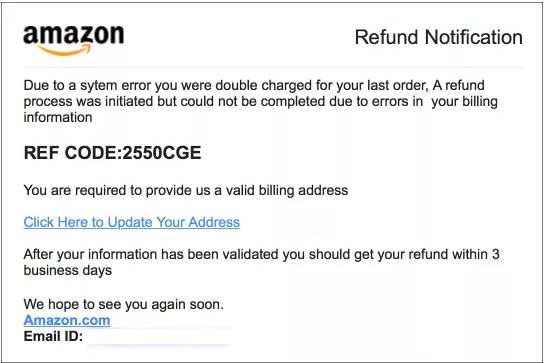
Holiday Scams
- Scammer takes advantage of people distracted in a holiday "daze" who will more likely give out their personal information.
- Includes 'too good to be true' deals on airfare, hotels, or expensive items.
- The scammer might also pose a friend or relative in need of immediate financial assistance in an emergency situation.
- Includes shipping notifications or purchase alerts on items you never purchased from major credit payment processors.
Examples of Seasonal Scams
How An IRS Scam Call Works - Video
Courtesy of The Majority Report w/Sam Sedar
Watch Sam Sedar speak with scammers impersonating IRS officials who claim he will be arrested if he doesn't pay the IRS back $5000.
If You Received a Seasonal Scam Email:
DO NOT click on any of the links or enter any information. Forward the email message to abuse@chapman.edu.